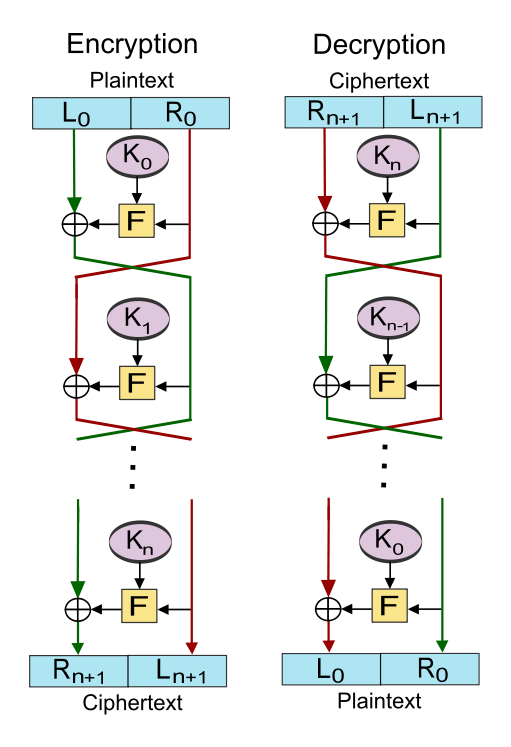
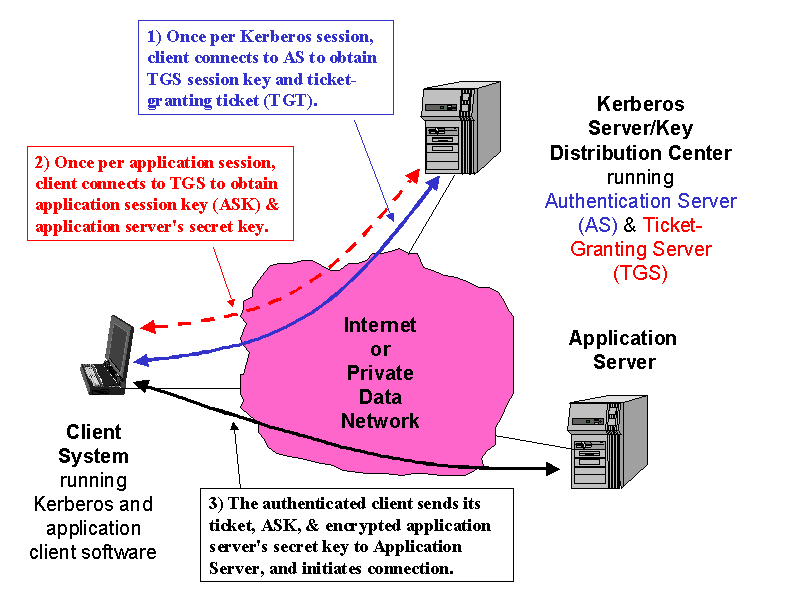
Define Cryptographic Primitives
Note however that the distinction between cryptographic primitives and cryptosystems is quite arbitrary. Its used by cryptographic designers as their most basic building blocks.
 Applied Cryptography In Net And Azure Key Vault A Practical Guide To Encryption In Net And Net Core Haunts Stephen 9781484243749 Amazon Com Books
Applied Cryptography In Net And Azure Key Vault A Practical Guide To Encryption In Net And Net Core Haunts Stephen 9781484243749 Amazon Com Books
Crypto system designers not being in a position to definitively prove their security must take the primitives they use as secure.
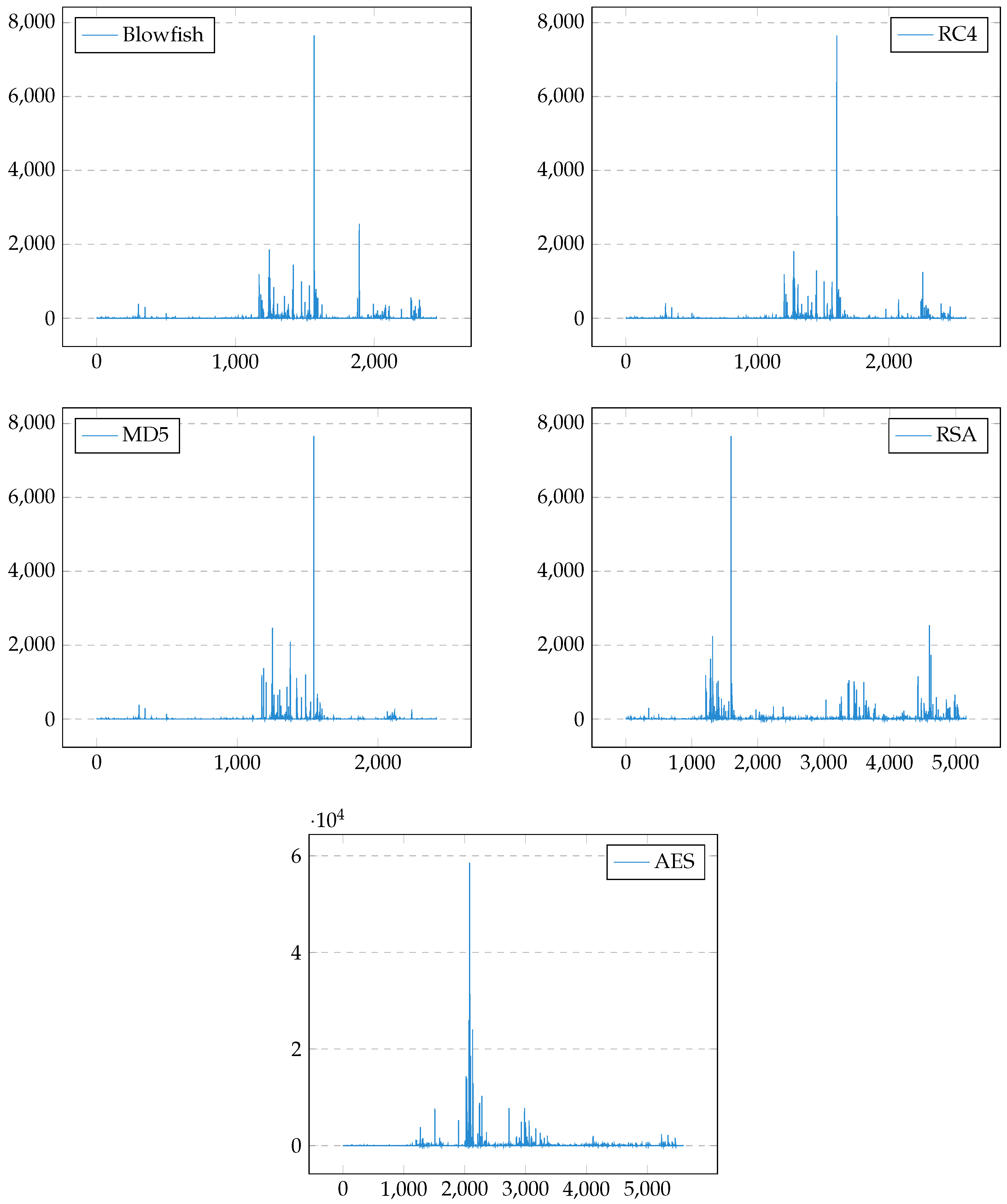
Define cryptographic primitives. A cryptographic primitive is a low level algorithm used to build cryptographic protocols for a security system. It is a method of storing and transmitting data in a particular form so that only those for whom it is intended can read and process it. Cryptographic primitives are demanding in terms of computation resources.
Cryptographic primitives are one of the building block of every crypto system eg tls ssl ssh etc. Choosing the best primitive available for use in a protocol usually provides the best available security. Cryptography is associated with the process of converting ordinary plain text into unintelligible text and vice versa.
With more consumer applications. They form the basic building blocks of modern cryptography. Crypto system designers not being in a position to definitively prove their security must take the primitives they use as secure.
Instead of primitives try to think tool cryptographic tools. However over time even well known cryptographic primitives lose their compliance status with the discovery of novel attacks that might either defeat the algorithm or reduce its robustness significantly. One or more cryptographic.
Examples of primitives include encryption schemes hash functions and digital signature schemes. They form the basic building blocks of modern cryptography. Choosing the best primitive available for use in a protocol usually provides the best available security.
Pseudorandom number generators feistel networks. Cryptography not only protects data from theft or alteration but can also be used for. This book describes a number of basic cryptographic tools primitives used to provide information security.
Typical examples of cryptographic primitives include pseudorandom functions one way functions etc. Modular mathematical functions that perform one task reliably. Examples include nonces one way functions salts and keys.
Cryptographic primitives are one of the building blocks of every crypto system eg tls ssl ssh etc. Cryptographic primitives are modular mathematical functions that perform one task reliably. Loose citation from handbook of applied cryptography.
Which of the following is used as a cryptographic primitive. Public key cryptography requires expensive exponentiations. Many cryptographic functions require random values that serve as seeds for further computation.
Cryptographic primitives are products of extensive reviews from cryptographers industry and government entities looking for any possible flaws. Secure hashes repeat iterative rounds of shifts and permutations. For example the rsa algorithm is sometimes considered a cryptosystem and sometimes a primitive.
These building blocks are a part of a cryptosystem which is a suite of cryptographic algorithms needed to. Symmetric ciphers use multiple iterations of dictionary lookups and permutations that are sequentially ordered.
Http Www Iacr Org Archive Crypto2000 18800377 18800377 Pdf
 Ppt White Box Cryptography Powerpoint Presentation Free Download Id 2198648
Ppt White Box Cryptography Powerpoint Presentation Free Download Id 2198648
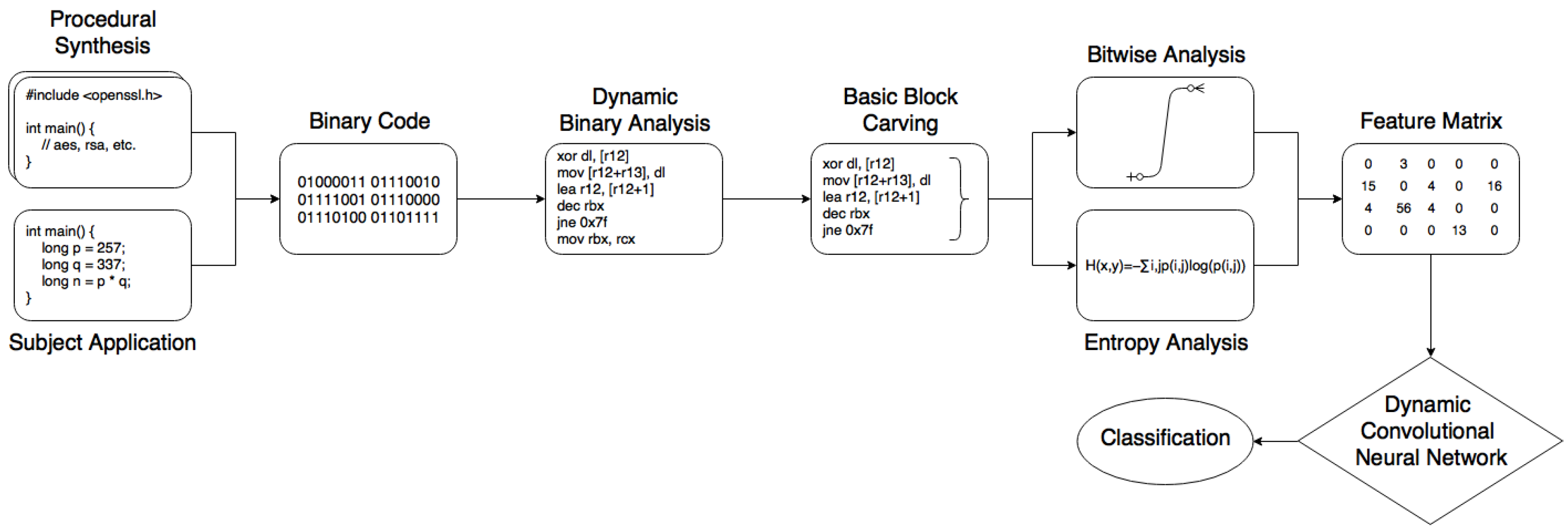 Information Free Full Text Cryptoknight Generating And Modelling Compiled Cryptographic Primitives Html
Information Free Full Text Cryptoknight Generating And Modelling Compiled Cryptographic Primitives Html
 Cryptography Tutorial App For Android Apk Download
Cryptography Tutorial App For Android Apk Download
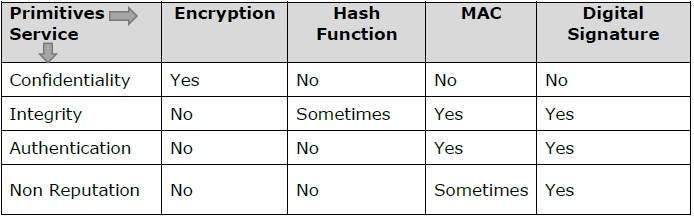 Modern Cryptography Tutorialspoint
Modern Cryptography Tutorialspoint
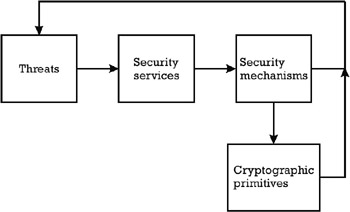 Appendix A Security Framework Implementing Electronic Card Payment Systems Artech House Computer Security Series
Appendix A Security Framework Implementing Electronic Card Payment Systems Artech House Computer Security Series
 Ppt Cryptographic Primitives Powerpoint Presentation Free Download Id 4597163
Ppt Cryptographic Primitives Powerpoint Presentation Free Download Id 4597163
 Pdf Cryptographic Primitives Enforcing Communication And Storage Complexity
Pdf Cryptographic Primitives Enforcing Communication And Storage Complexity
 Figure 1 From Secret Key Authentication Beyond The Challenge Response Paradigm Definitional Issues And New Protocols Semantic Scholar
Figure 1 From Secret Key Authentication Beyond The Challenge Response Paradigm Definitional Issues And New Protocols Semantic Scholar
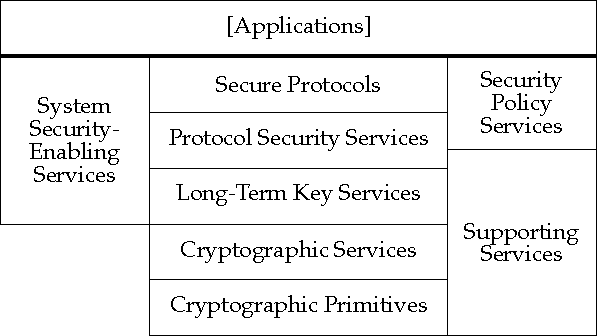 Architecture For Public Key Infrastructure Apki Public Key Infrastructure Components
Architecture For Public Key Infrastructure Apki Public Key Infrastructure Components
 Pdf Automated Identification Of Cryptographic Primitives In Binary Programs
Pdf Automated Identification Of Cryptographic Primitives In Binary Programs
 Ldapwiki Cryptographic Primitive
Ldapwiki Cryptographic Primitive
 Message Authentication Code Wikipedia
Message Authentication Code Wikipedia
Http Www Cs Cornell Edu Rafael Papers Nonbb Pdf
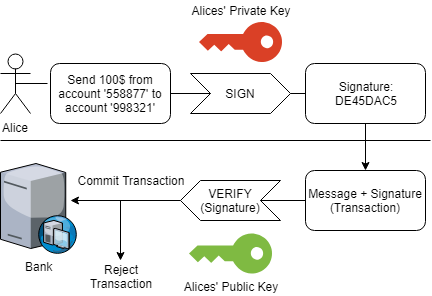 Blockchain Common Cryptographic Primitives By Adrian Bednarek Independent Security Evaluators
Blockchain Common Cryptographic Primitives By Adrian Bednarek Independent Security Evaluators
Https Www Esat Kuleuven Be Cosic Publications Article 3041 Pdf
 Information Free Full Text Cryptoknight Generating And Modelling Compiled Cryptographic Primitives Html
Information Free Full Text Cryptoknight Generating And Modelling Compiled Cryptographic Primitives Html
 Pdf Cryptography In Gpus Samuel Neves Academia Edu
Pdf Cryptography In Gpus Samuel Neves Academia Edu
 On The Bit Security Of Cryptographic Primitives By Michael Walter
On The Bit Security Of Cryptographic Primitives By Michael Walter
 On The Bit Security Of Cryptographic Primitives By Michael Walter
On The Bit Security Of Cryptographic Primitives By Michael Walter
 On The Bit Security Of Cryptographic Primitives By Michael Walter
On The Bit Security Of Cryptographic Primitives By Michael Walter
 On The Bit Security Of Cryptographic Primitives By Michael Walter
On The Bit Security Of Cryptographic Primitives By Michael Walter
 2 Taxonomy Of Cryptographic Primitives Download Scientific Diagram
2 Taxonomy Of Cryptographic Primitives Download Scientific Diagram
Symmetric Key Algorithm In Cryptography By Quantum Backdoor Medium
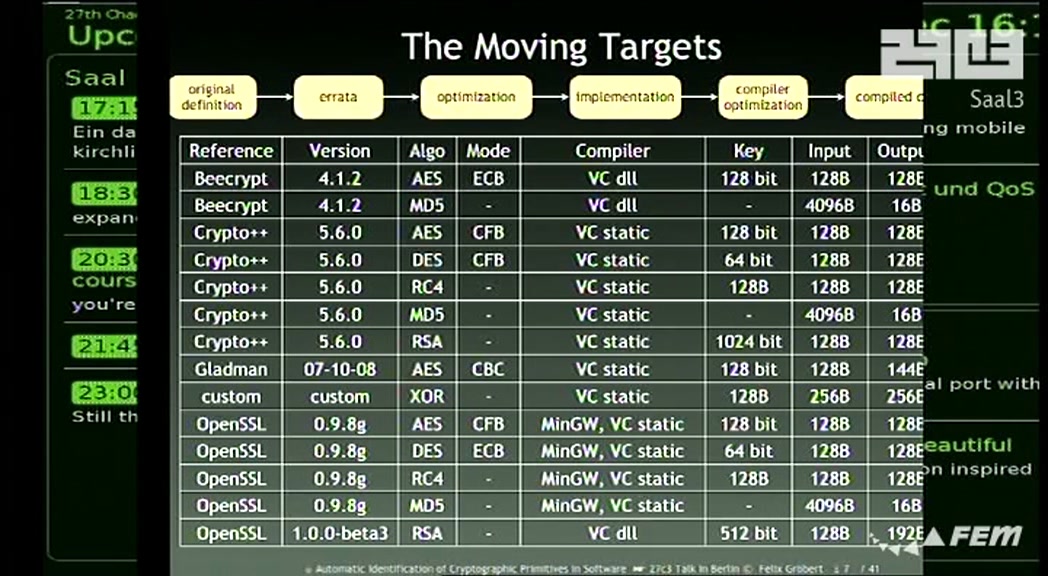 Media Ccc De Automatic Identification Of Cryptographic Primitives In Software
Media Ccc De Automatic Identification Of Cryptographic Primitives In Software
 Cryptographic Primitives Mastering Blockchain Second Edition
Cryptographic Primitives Mastering Blockchain Second Edition
Https Nvlpubs Nist Gov Nistpubs Ir 2020 Nist Ir 8214a Pdf