Blockchain 51 Attack Proof Of Stake
Blockchain 51 Attack Proof Of Stake. The cartel had to be punished whenever validators appeared to be missing. A 51 percent attack describes an event where the majority of hash rate in a network is controlled by a sole entity.
From that point, the attacker could create fraudulent transactions with the intention of benefiting themselves or robbing a. The hash power is more critical in the attacks. If you could attack or damage the blockchain creation tools on a.
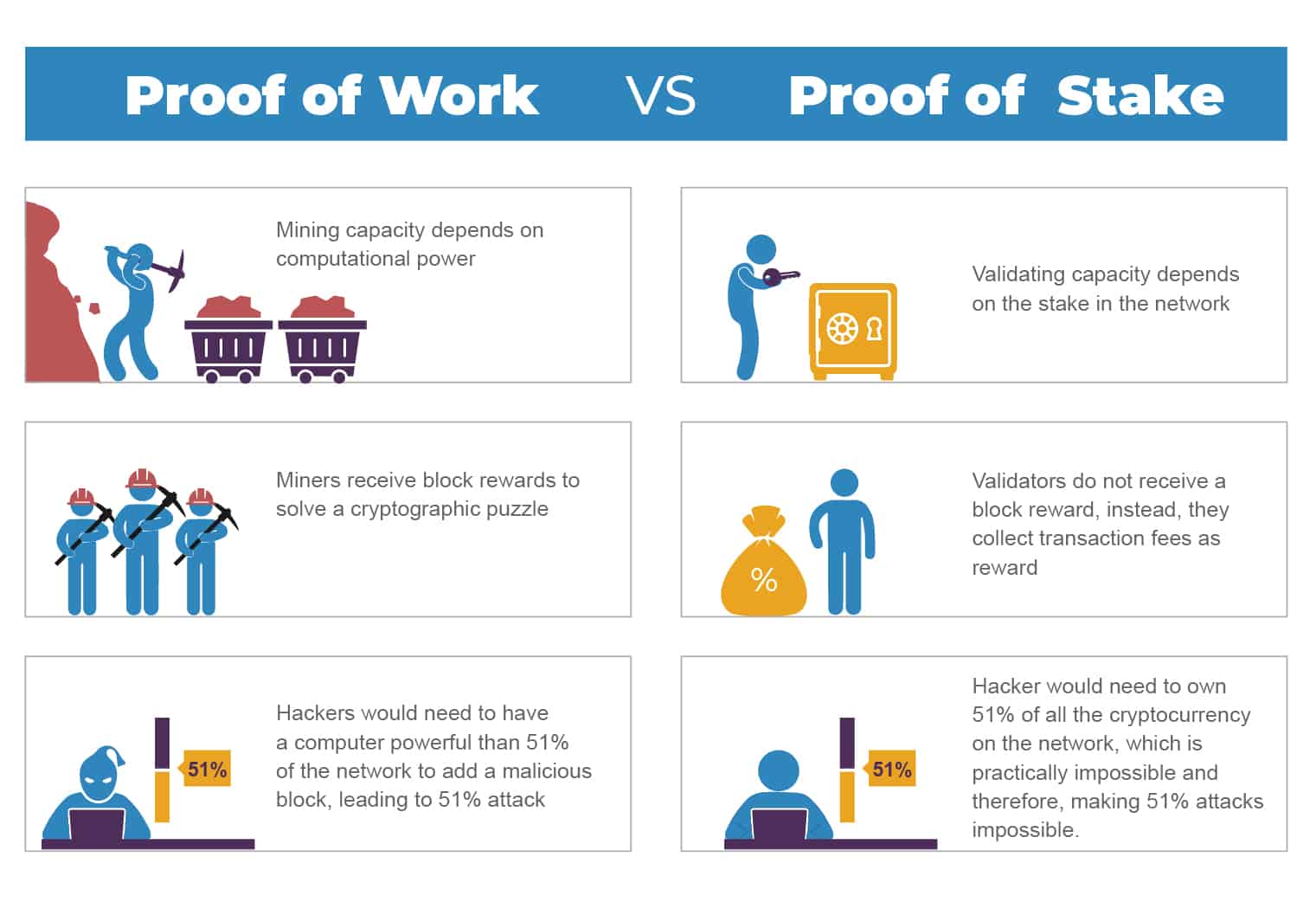
In Other Words, If Malicious Users Want To Perform A 51% Attack On A Pos Network, They Would Need To Own 51% Of The Cryptocurrency, Which Will Be Quite Difficult And.
This would theoretically give that individual complete control over the network's consensus mechanism. The attack’s impact can be mild or severe, depending on the mining power of the attacker. You give a permission to access the blockchain only parties you know (consortium).
Due To The Immense Attacking.
How proof of stake renders a 51% attack unlikely and unappealing. From that point, the attacker could create fraudulent transactions with the intention of benefiting themselves or robbing a. Once purely theoretical, “majority” or “51%” attacks on public blockchains have dealt participants a reality check:
Can A Proof Of Stake Mechanism Help You Avoid A 51% Attack?
Then, should they choose, they can abuse their majority share and effectively “hijack” the blockchain. Although it would be difficult and expensive to accumulate 51% of a reputable digital coin, a staker with 51% stake in the coin would not have it in her best interest to attack a network that they hold a. The hash power is more critical in the attacks.
Benefits Of Blockchain Proof Of Stake In Preventing Cyberattacks.
You know the identity of these parties. If any of the parties misbehave they are kicked out of the consortium. In a 51% attack, one miner or mining group gains or purchases enough hash power to take control of.
In A Similar Way, N Confirmation And Selfish Mining Are Two Attack Techniques That Comprise A Similar Strategy To The 51% Attack.
A 51% attack, also known as a majority attack, occurs when a single person or group of people gains control of over 50% of a blockchain’s hashing power. If you could attack or damage the blockchain creation tools on a. Adversaries controlling more than half of the total hashing power of a network can perform this attack.
