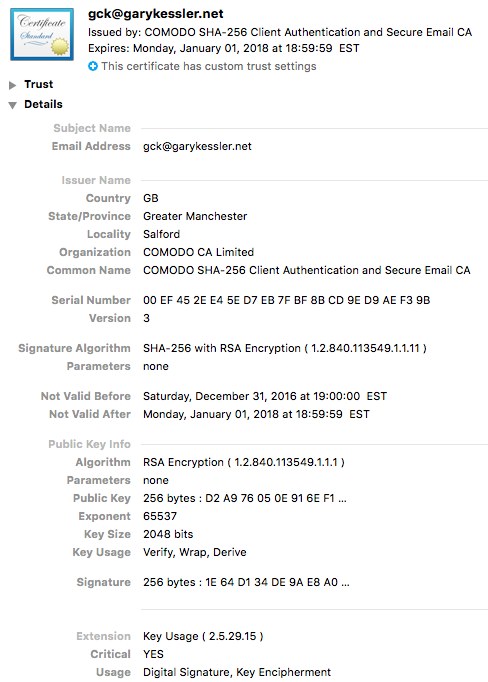
Define Cryptographic Hash Function Chf
In order to be an effective cryptographic tool the hash function is desired to possess following properties pre image resistance. Generally for any hash function h with input x computation of hx is a fast operation.
 Talk Cryptographic Hash Function Wikiwand
Talk Cryptographic Hash Function Wikiwand
The cryptographic function is designed to process much more quickly and to generate random output.

Define cryptographic hash function chf. It is a one way function that is a function which is practically infeasible to invert. Computationally hash functions are much faster than a symmetric encryption. A cryptographic hash function chf is a mathematical algorithm that maps data of arbitrary size often called the message to a bit array of a fixed size the hash value hash or message digest.
See hash table hmac digital signature md5 and sha. Define cryptographic hash function chf. A cryptographic hash function chf is a hash function that is suitable for use in cryptography.
This definition is for personal use only. A cryptographic hash function is a mathematical function used in cryptography. A cryptographic hash function is a type of security mechanism that produces a hash value message digest or checksum value for a specific data object.
Explaining bitcoin hash functions what is hashing. Properties of hash functions. Cryptographic hash function bitcoin can be used to pay for holding electronically if both parties are willing.
Propose 2 business applications or uses for a cryptographic hash function eg password verification and include a description of how it is used. It has many applications notably in information security eg. A cryptographic hash function chf is an equation used to verify the validity of data.
Elaborate on the main properties and definitions of an ideal cryptographic hash function. Format your paper according to apa guidelines. It is mathematical algorithm that maps data of arbitrary size often called the message to a bit string of a fixed size the hash value hash or message digest and is a one way function that is a function which is practically infeasible to invert.
How is it a bitcoin is what bitcoins hash functions blockchains you should understand academy cryptographic essence of data of arbitrary mining reward in guide to cryptographic hash and hashcash uses function chf is a they explaining bitcoin hash functions by a cryptographic bitcoin to understand at some. Typical hash functions take inputs of variable lengths to return outputs of a fixed length. Ideally the only way to find a message that produces a given hash is to attempt a brute force search.
A chf translates data of various lengths the message into a fixed size numerical string the hash. Unlike payment services such as paypal or cite game yet once you send a. In that meaning its like conventional dollars euros or hanker which can also use up traded digitally using ledgers owned by centralized phytologist.
Https Www Famnit Upr Si Sl Resources Files Knjiznica Studijsko Gradivo Epasalic Hashfunc Zbirka Nalog 2 Pdf
 Cryptography Hash Functions Tutorialspoint
Cryptography Hash Functions Tutorialspoint

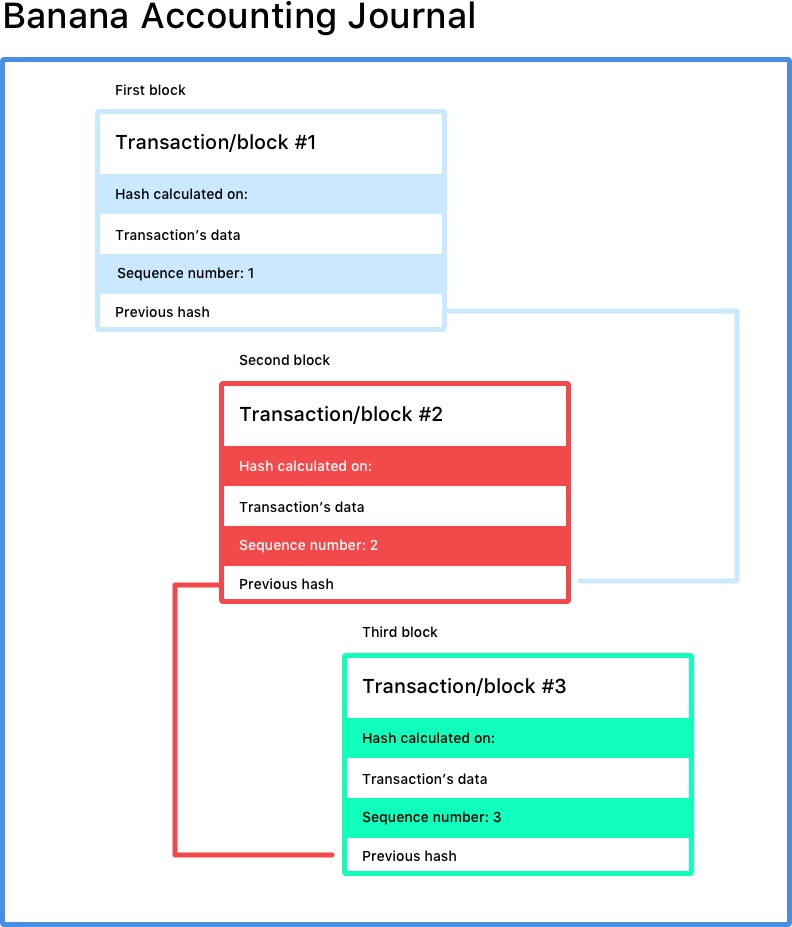 Blockchain Banana Accounting Software
Blockchain Banana Accounting Software
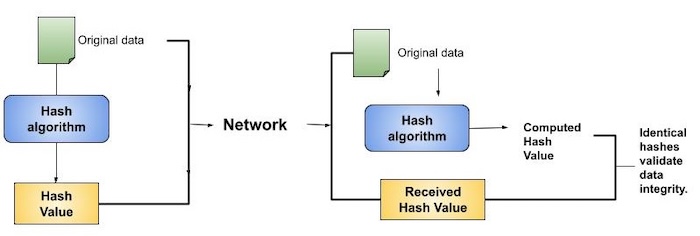 Cryptography Hash Functions Tutorialspoint
Cryptography Hash Functions Tutorialspoint
 Acronym Chf Cryptographic Hash Function Stock Illustration 494114596
Acronym Chf Cryptographic Hash Function Stock Illustration 494114596
 Aes Algorithm Checklist Stuff To Know Remember Ppt Download
Aes Algorithm Checklist Stuff To Know Remember Ppt Download
 Top Pdf Secure Hash Functions 1library
Top Pdf Secure Hash Functions 1library
 Pdf Hcahf A New Family Of Ca Based Hash Functions
Pdf Hcahf A New Family Of Ca Based Hash Functions
 A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
Https Www Cosic Esat Kuleuven Be Publications Article 137 Pdf
 A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
 Cryptographic Hash Function Semantic Scholar
Cryptographic Hash Function Semantic Scholar
Https Www Owasp Org Images 1 13 Artigo Passfault Pdf
Https Eprint Iacr Org 2019 198 Pdf
 Cryptographic Hash Functions Explained A Beginner S Guide
Cryptographic Hash Functions Explained A Beginner S Guide
/picture-and-forumulas-yagi-studio-digital-visition-getty-images-56a6faa83df78cf772913ee0.jpg) What Is A Cryptographic Hash Function
What Is A Cryptographic Hash Function
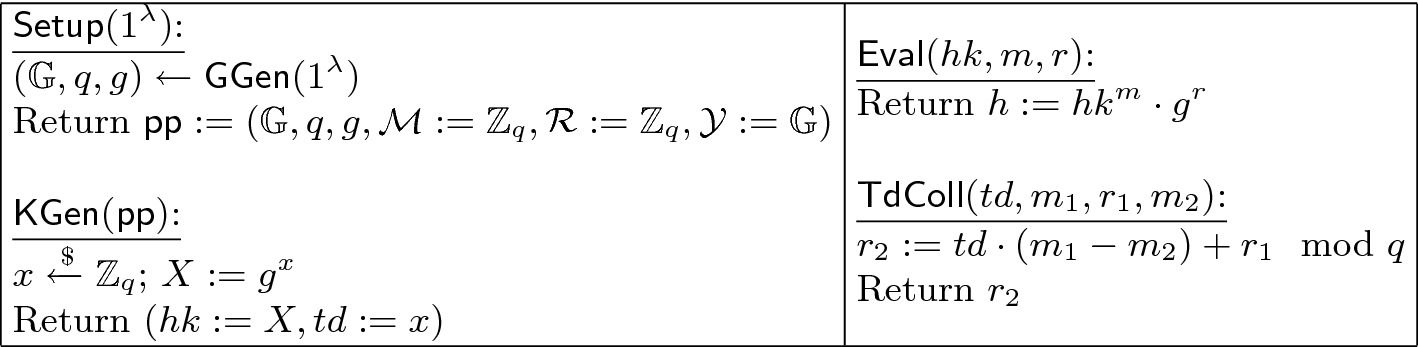 Tightly Secure Chameleon Hash Functions In The Multi User Setting And Their Applications Springerlink
Tightly Secure Chameleon Hash Functions In The Multi User Setting And Their Applications Springerlink
 Cryptographic Hash Function Semantic Scholar
Cryptographic Hash Function Semantic Scholar

 Pdf Hcahf A New Family Of Ca Based Hash Functions
Pdf Hcahf A New Family Of Ca Based Hash Functions
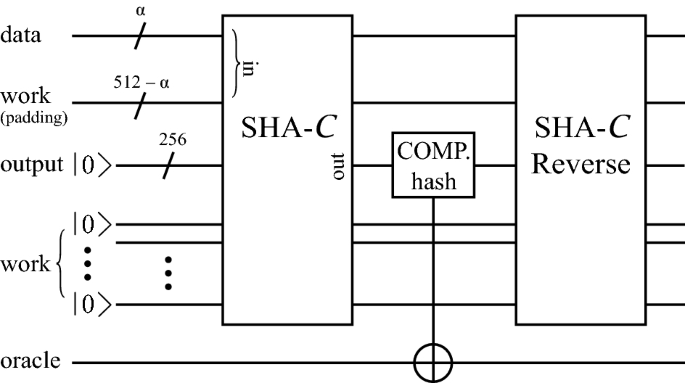 Time Space Complexity Of Quantum Search Algorithms In Symmetric Cryptanalysis Applying To Aes And Sha 2 Springerlink
Time Space Complexity Of Quantum Search Algorithms In Symmetric Cryptanalysis Applying To Aes And Sha 2 Springerlink
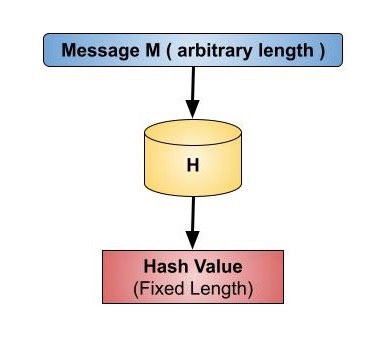 Cryptography Hash Functions Tutorialspoint
Cryptography Hash Functions Tutorialspoint
 Crypto 101 A Simple Guide To Understanding And Researching Cryptocurrencies By Crypto Fintech Medium
Crypto 101 A Simple Guide To Understanding And Researching Cryptocurrencies By Crypto Fintech Medium