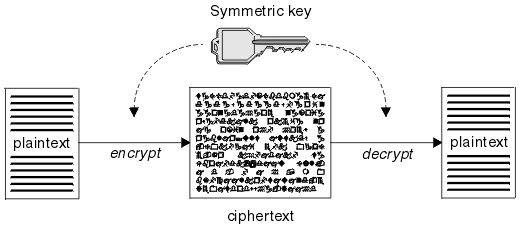
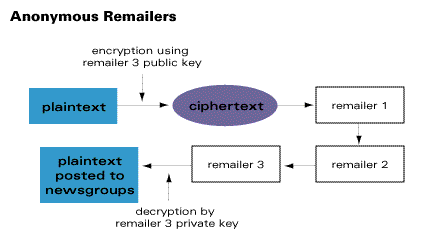
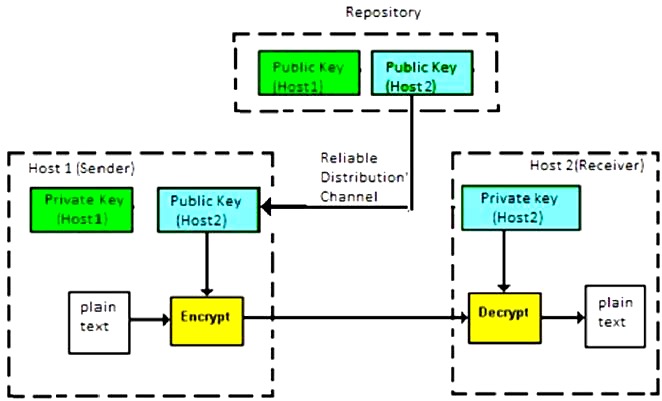
Define Public Key Cryptography
A public key is created in public key encryption cryptography that uses asymmetric key encryption algorithms. Unlike symmetric key cryptography we do not find historical use of public key cryptography.
 All About Ssl Cryptography Digicert Com
All About Ssl Cryptography Digicert Com
Unlike symmetric key algorithms that rely on one key to both encrypt and decrypt each key performs a unique function.

Define public key cryptography. Symmetric cryptography was well suited for organizations such as governments military and big financial corporations were involved in the classified communication. Public key cryptography uses a pair of keys to encrypt and. In cryptography a public key is a large numerical value that is used to encrypt data.
Sometimes referred to as asymmetric cryptography public key cryptography is a class of cryptographic protocols based on algorithms. Public keys are used to convert a message into an unreadable format. Meaning of public key cryptography.
Public key cryptography also known as asymmetric cryptography is a popular encryption method developed by martin hellman and whitfield diffie in 1976 that is used for securing the transmission of data over distrusted networks such as the internet. Public key cryptography pkc is an encryption technique that uses a paired public and private key or asymmetric key algorithm for secure data communication. Public key cryptography or asymmetric cryptography is an encryption scheme that uses two mathematically related but not identical keys a public key and a private key.
Public key cryptography or asymmetric cryptography is a cryptographic system that uses pairs of keys. Public keys which may be disseminated widely and private keys which are known only to the ownerthe generation of such keys depends on cryptographic algorithms based on mathematical problems to produce one way functionseffective security only requires keeping the private key private. Decryption is carried out using a different but matching private key.
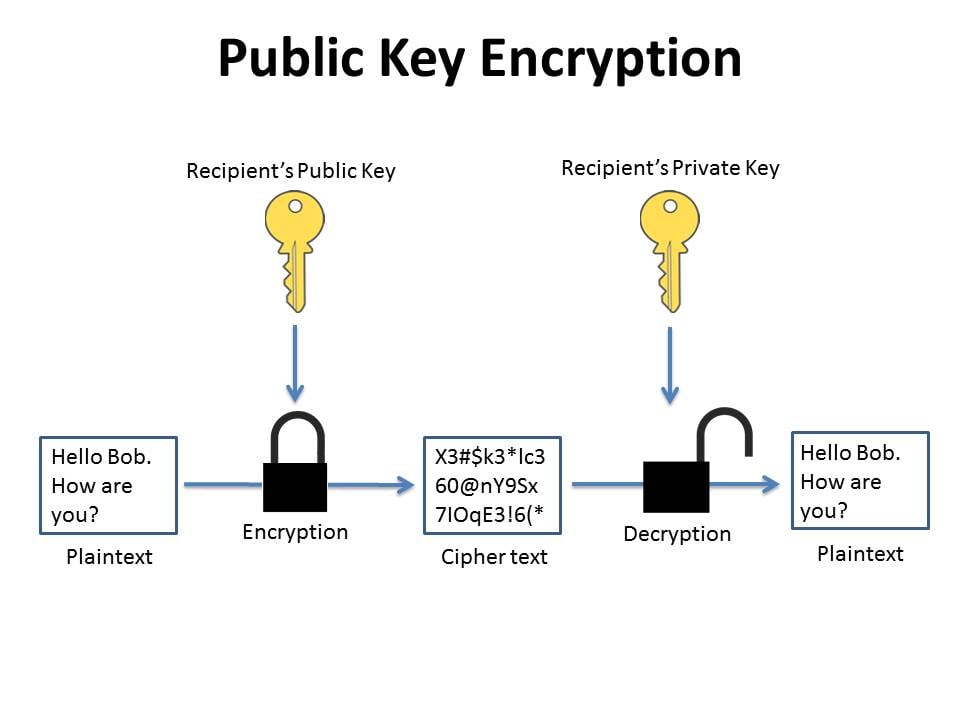
A message sender uses a recipients public key to encrypt a message. It is a relatively new concept. The key can be generated by a software program but more often it is provided by a trusted designated.
Public and private keys are paired to enable secure communication. Definition of public key cryptography in the network encyclopedia. This method of cryptography requires two separate keys one that is private or secret and one that is public.
A definition of public key cryptography. To decrypt the senders message only the recipients private key may be used. Information and translations of public key cryptography in the most comprehensive dictionary definitions resource on the web.
What does public key cryptography mean. What is public key cryptography.
Https Encrypted Tbn0 Gstatic Com Images Q Tbn And9gcqgidkmps8kez8bezopkgryy33fket6rgsbv6vedejf3gokzeqx Usqp Cau
 Encrypting Vs Signing With Openpgp What S The Difference
Encrypting Vs Signing With Openpgp What S The Difference
 Si110 Asymmetric Public Key Cryptography
Si110 Asymmetric Public Key Cryptography
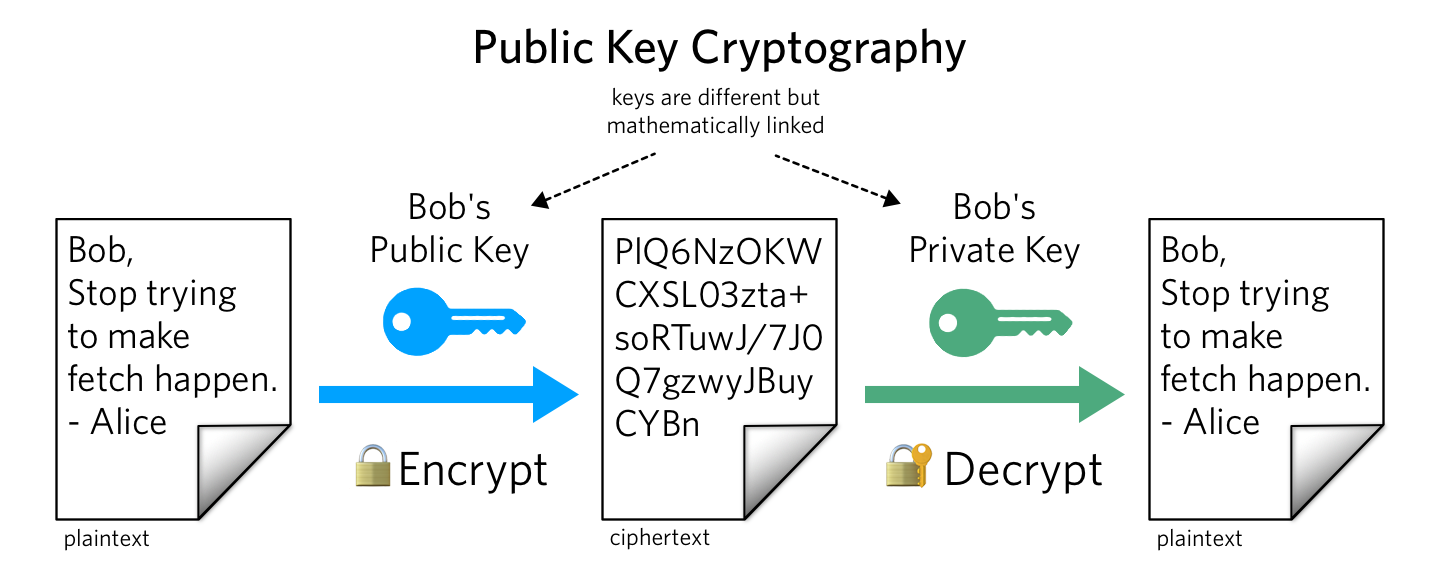
Si110 Asymmetric Public Key Cryptography
 Pdf A Public Key Cryptosystem Based Upon Euclidean Addition Chains
Pdf A Public Key Cryptosystem Based Upon Euclidean Addition Chains
 Definition Of Cryptography Pcmag
Definition Of Cryptography Pcmag
 Public Key Cryptography Wikipedia
Public Key Cryptography Wikipedia
 A Deep Dive On End To End Encryption How Do Public Key Encryption Systems Work Surveillance Self Defense
A Deep Dive On End To End Encryption How Do Public Key Encryption Systems Work Surveillance Self Defense


 Public Key Vs Private Key Public Key Cryptography Explained Sectigo Official
Public Key Vs Private Key Public Key Cryptography Explained Sectigo Official
 What Are Public Keys And Private Keys Ledger
What Are Public Keys And Private Keys Ledger
 What Are Public Keys And Private Keys Ledger
What Are Public Keys And Private Keys Ledger
 What Is Private Key Encryption Koolspan
What Is Private Key Encryption Koolspan
 Vegetarian Pig Lover A History Of Codes And Ciphers In Code And Cipher
Vegetarian Pig Lover A History Of Codes And Ciphers In Code And Cipher
 Token Security Cryptography Part 2 Blockchainhub
Token Security Cryptography Part 2 Blockchainhub
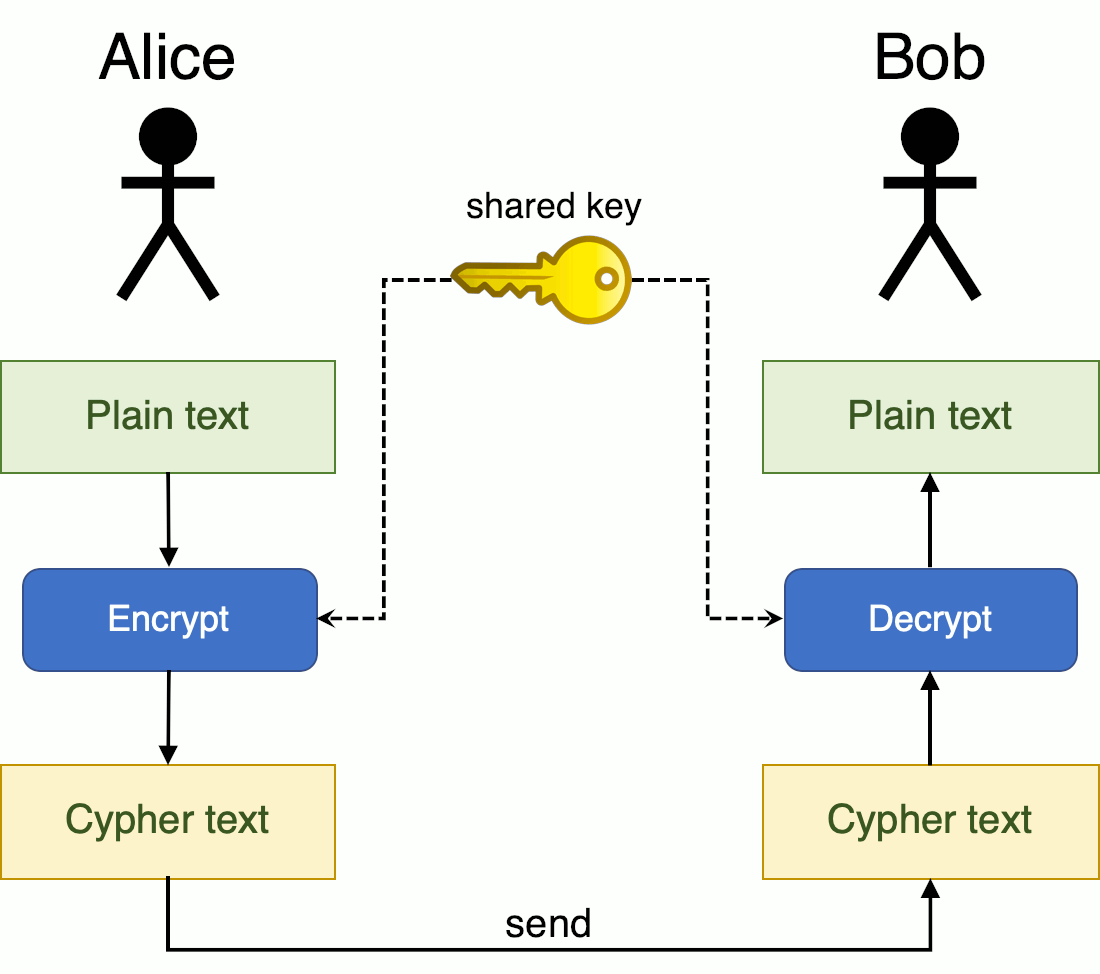 How To Survive An Infosec Job Interview Cryptography
How To Survive An Infosec Job Interview Cryptography
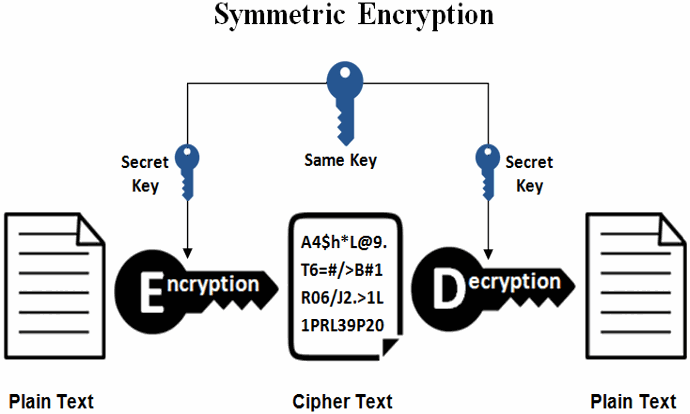 Encryption Symmetric And Asymmetric Practical Cryptography For Developers
Encryption Symmetric And Asymmetric Practical Cryptography For Developers
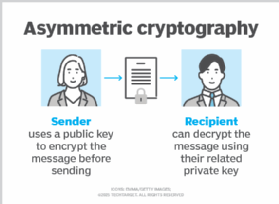 What Is Asymmetric Cryptography And How Does It Work
What Is Asymmetric Cryptography And How Does It Work
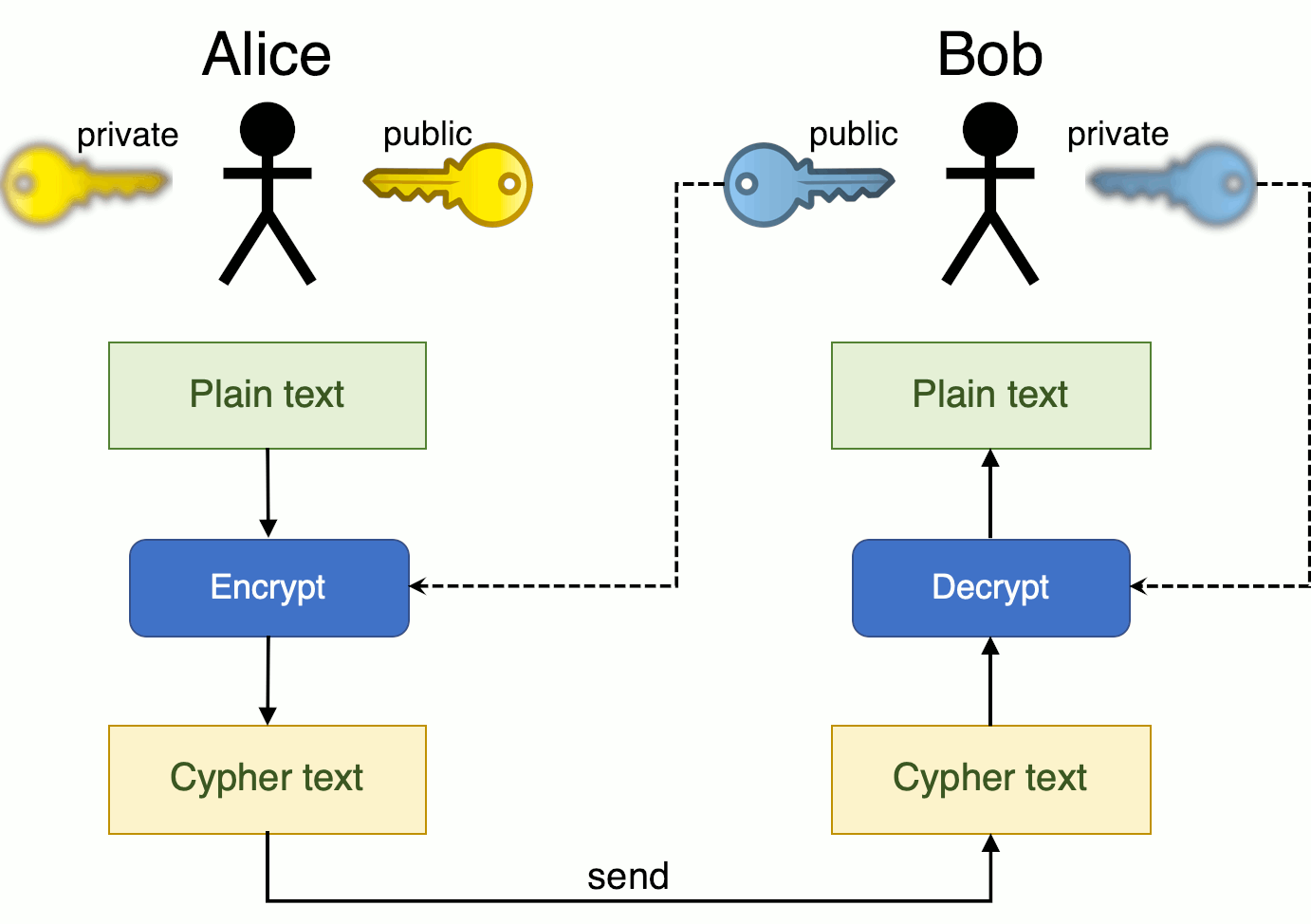 How To Survive An Infosec Job Interview Cryptography
How To Survive An Infosec Job Interview Cryptography
 What Is Public Key Cryptography How Does It Work And What Are Its Uses
What Is Public Key Cryptography How Does It Work And What Are Its Uses
 Public Key Cryptosystems An Overview Sciencedirect Topics
Public Key Cryptosystems An Overview Sciencedirect Topics
 A Deep Dive On End To End Encryption How Do Public Key Encryption Systems Work Surveillance Self Defense
A Deep Dive On End To End Encryption How Do Public Key Encryption Systems Work Surveillance Self Defense
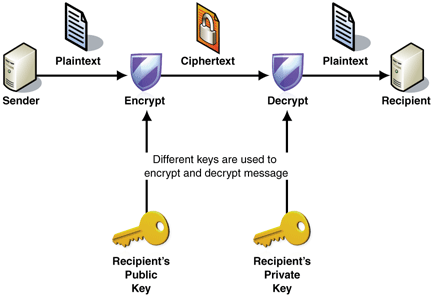 Symmetric And Asymmetric Key Cryptography In Hindi
Symmetric And Asymmetric Key Cryptography In Hindi
 A Deep Dive On End To End Encryption How Do Public Key Encryption Systems Work Surveillance Self Defense
A Deep Dive On End To End Encryption How Do Public Key Encryption Systems Work Surveillance Self Defense
 What Is A Public And Private Key Pair
What Is A Public And Private Key Pair
Difference Between Public Key And Private Key In Cryptography Pediaa Com