Define Cryptographic Hash Function Cfh
Password verification and a description of. The cryptographic function is designed to process much more quickly and to generate random output.
Https Eprint Iacr Org 2017 240 Pdf
Cryptographic hash function bitcoin can be used to pay for holding electronically if both parties are willing.

Define cryptographic hash function cfh. A cryptographic hash function chf is a mathematical algorithm that maps data of arbitrary size often called the message to a bit array of a fixed size the hash value hash or message digest. See hash table hmac digital signature md5 and sha. Format your paper according to appropriate course level apa guidelines.
Give at least 2 applications or uses for a cfh example. List and define the main properties of an ideal cryptographic hash function. It is a one way function that is a function which is practically infeasible to invert.
You may remember learning a few equations in high school such as linear equations of the form ymxb or quadratic equations of the form yax 2 bxc. Password verification and a description of how it is used. This definition is for personal use only.
Ideally the only way to find a message that produces a given hash is to attempt a brute force search. A cryptographic hash function is a type of security mechanism that produces a hash value message digest or checksum value for a specific data object. Password verification and a brief description of how it is used.
In that meaning its like conventional dollars euros or hanker which can also use up traded digitally using ledgers owned by centralized phytologist. A brief overview of cryptographic hash functions. A cryptographic hash function is more or less the same thing.
A cryptographic hash function is just a mathematical equation. List and define and explain the main properties of an ideal cryptographic hash function. Define and thoroughly describe cryptographic hash function cfh.
Unlike payment services such as paypal or cite game yet once you send a. List and define and explain the main properties of an ideal cryptographic hash function. Give at least 2 applications or uses for a cfh example.
Define and thoroughly describe cryptographic hash function cfh. Answer the following in a 2 to 3 page apa formatted paper. Define cryptographic hash function cfh.
Give at least 2 applications or uses for a cfh example.
 Translation Of Algorithmic Descriptions Of Discrete Functions To Sat With Applications To Cryptanalysis Problems
Translation Of Algorithmic Descriptions Of Discrete Functions To Sat With Applications To Cryptanalysis Problems
 Translation Of Algorithmic Descriptions Of Discrete Functions To Sat With Applications To Cryptanalysis Problems
Translation Of Algorithmic Descriptions Of Discrete Functions To Sat With Applications To Cryptanalysis Problems
Https Edps Europa Eu Sites Edp Files Publication 19 10 30 Aepd Edps Paper Hash Final En Pdf
 A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
 A Deep Dive Into Cryptographic Hash Functions Kingsland University
A Deep Dive Into Cryptographic Hash Functions Kingsland University
 A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
 A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
 Pdf Open Sesame The Password Hashing Competition And Argon2
Pdf Open Sesame The Password Hashing Competition And Argon2
 A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
Https Encrypted Tbn0 Gstatic Com Images Q Tbn And9gcqz U58bavaphm4pxephzxtcmzpathg7tua0 4n0abjgcahk2hc Usqp Cau
/picture-and-forumulas-yagi-studio-digital-visition-getty-images-56a6faa83df78cf772913ee0.jpg) What Is A Cryptographic Hash Function
What Is A Cryptographic Hash Function
Https Edps Europa Eu Sites Edp Files Publication 19 10 30 Aepd Edps Paper Hash Final En Pdf
Http Www Iacr Org Archive Asiacrypt2016 10031238 10031238 Pdf
/picture-and-forumulas-yagi-studio-digital-visition-getty-images-56a6faa83df78cf772913ee0.jpg) What Is A Cryptographic Hash Function
What Is A Cryptographic Hash Function
 What Are Cryptographic Hash Functions Synopsys
What Are Cryptographic Hash Functions Synopsys
Https Core Ac Uk Download Pdf 51697689 Pdf
Https Edps Europa Eu Sites Edp Files Publication 19 10 30 Aepd Edps Paper Hash Final En Pdf
 A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
Https Smookingarea Files Wordpress Com 2015 04 Cehv8 Module 19 Cryptography Pdf
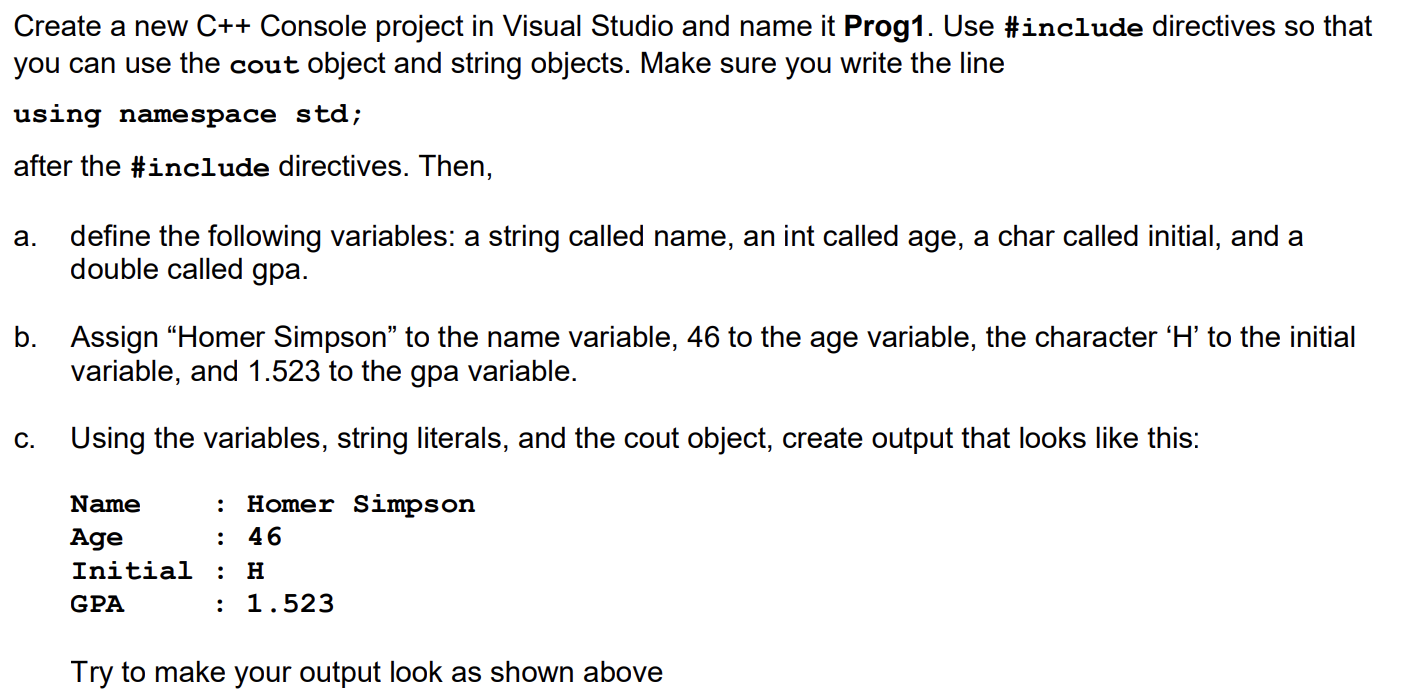 Answered Create A New C Console Project In Bartleby
Answered Create A New C Console Project In Bartleby
 A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
 A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
:max_bytes(150000):strip_icc()/picture-and-forumulas-yagi-studio-digital-visition-getty-images-56a6faa83df78cf772913ee0.jpg) What Is A Cryptographic Hash Function
What Is A Cryptographic Hash Function
 A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
A New Design Paradigm For Provably Secure Keyless Hash Function With Subsets And Two Variables Polynomial Function Sciencedirect
Https Www Ics Uci Edu Keldefra Teaching Fall2016 Uci Compsci134 Slides Lec5 Ked Pdf
Https Edps Europa Eu Sites Edp Files Publication 19 10 30 Aepd Edps Paper Hash Final En Pdf
 Nhs Informatics Architecture Approved Cryptographic Algorithms Good Practice Guideline
Nhs Informatics Architecture Approved Cryptographic Algorithms Good Practice Guideline
 Translation Of Algorithmic Descriptions Of Discrete Functions To Sat With Applications To Cryptanalysis Problems Deepai
Translation Of Algorithmic Descriptions Of Discrete Functions To Sat With Applications To Cryptanalysis Problems Deepai
 Apply Cryptographic Hash Function Docx Apply U2013 Cryptographic Hash Function Apply U2013 Cryptographic Hash Function Dat 305 Professor William Mcknown Course Hero
Apply Cryptographic Hash Function Docx Apply U2013 Cryptographic Hash Function Apply U2013 Cryptographic Hash Function Dat 305 Professor William Mcknown Course Hero
 Apply Cryptographic Hash Function Docx Apply U2013 Cryptographic Hash Function Apply U2013 Cryptographic Hash Function Dat 305 Professor William Mcknown Course Hero
Apply Cryptographic Hash Function Docx Apply U2013 Cryptographic Hash Function Apply U2013 Cryptographic Hash Function Dat 305 Professor William Mcknown Course Hero
:max_bytes(150000):strip_icc()/GettyImages-748345923-8be7972bb1fc4e06a0218edaea7d8abd.jpg) Cryptographic Hash Functions Definition
Cryptographic Hash Functions Definition
 Dat 305 Wk 1 Apply Create A Table Of Sorting Algorithms Https Uopcourse Com Category Dat 305
Dat 305 Wk 1 Apply Create A Table Of Sorting Algorithms Https Uopcourse Com Category Dat 305
